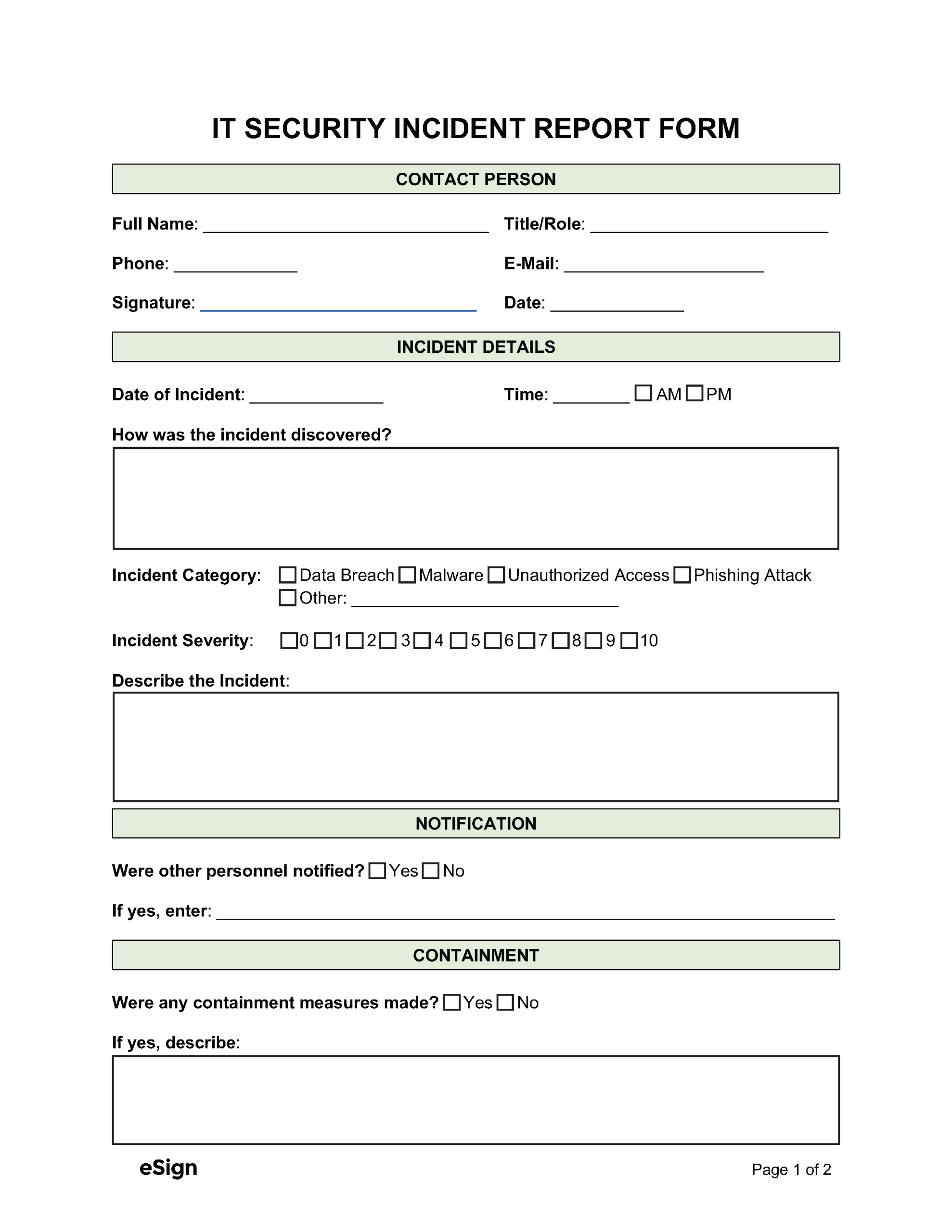
An IT security incident report documents the particulars of a cyber attack on an organization’s networks, systems, or data. The report describes how and when the issue was found, the nature and extent of the breach, and the actions that were taken in response to the threat. After being completed, the report is kept in the company’s internal records for future reference.
AKA
- Cybersecurity Incident Report
- Databreach Incident Report
- Cyber Attack Incident Report
Reporting a Cybercrime
Victims of internet-based fraud, scams, and other cybercrimes can file complaints with the Internet Crime Complaint Center (IC3). Ongoing crimes, threats to life, or terrorist threats attacks can be reported to the FBI by filling out an Online Tip Form or contacting a local field office.
If Protected Health Information (PHI) was compromised in a cybersecurity breach, the incident must be reported to the HSS.
Incident Examples
- Data or information breach
- Malware, ransomware, and denial-of-service (DDoS)
- Unauthorized access
- Phishing attacks
Sample
Full Name: [FULL NAME] Title/Role: [TITLE/ROLE]
Signature: Date: [MM/DD/YYYY]
Location: [LOCATION]
How was the incident discovered? [DESCRIBE DISCOVERY OF INCIDENT]
Incident Severity: ☐ 0 ☐ 1 ☐ 2 ☐ 3 ☐ 4 ☐ 5 ☐ 6 ☐ 7 ☐ 8 ☐ 9 ☐ 10
Describe the Incident: [DESCRIBE THE INCIDENT]
If yes, enter: [LIST CONTACTED PERSONNEL]
If yes, describe: [DESCRIBE CONTAINMENT MEASURES]
If yes, describe: [DESCRIBE IMPACTED SERVICES]
If yes, describe: [DESCRIBE ATTACK]
INFORMATION IMPACT
Was there any breach of data, records, or information? ☐ Yes ☐ No
If yes, describe: [DESCRIBE BREACHES]
ADDITIONAL INFORMATION
Is there any other information that should be provided? ☐ Yes ☐ No
If yes, describe: [DESCRIBE ADDITIONAL INFORMATION]